-
Cyberattacks in the cloud take minutes rather than days in on-premise environments.
-
Threat actors are abusing IAM to exploit the cloud’s complex environment.
-
Sysdig notes new infrastructure-as-code (IaC)-based defenses are ineffective.
The cyber arms race has officially gone airborne.
Attackers continue to fine-tune their techniques to get what they want in the cloud, now spending just ten minutes staging a threat versus 16 days in on-premise environments, according to a new global threat report from Sysdig.
With “lightning fast” cloud attacks on the rise, “threat detection needs to have a complete view, with the ability to track threats across multiple environments,” when dancing the fine line between a threat’s safe detection and severe damage, according to Sysdig.
Every minute, second counts
Attackers are abusing cloud services and policies in order to exploit the cloud’s complex environment. That’s because in an “everything as code” world, a simple syntax error could ultimately lead to a company’s breach splashed across the next day’s paper.
Identity and access management (IAM) is a key cloud security control that attackers are closing in on to strengthen their techniques for credential access, privilege escalation and lateral movement.
S3 buckets — a public cloud storage resource — are especially popular for storing secrets and keys, according to Sysdig, and threat actors like TeamTNT are constantly exploiting vulnerable applications in cloud credentials.
Automation’s weaponization
It’s pretty common to misplace secrets, and Sysdig points to new infrastructure-as-code (IaC) -based defenses as simply ineffective. Notably, Amazon Web Services’ (AWS) CloudFormation, the AWS service for IaC, is an ideal feature for attackers to abuse.
In a recent January 2022 attack, CloudFormation was “configured to allow attackers to access it and attempt to run malicious templates.”
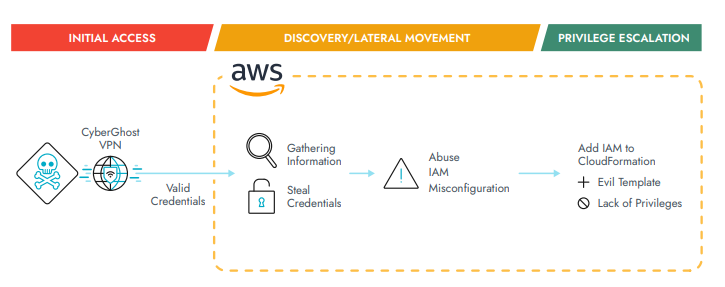
Organizations can lower the possibilities of credential leaks by implementing a secrets management system, according to Sysdig. This way keys and credentials are stored in a centralized location and require an API for retrieval instead of being left up for grabs in files for attackers to munch on.
Cloud service providers (CSPs) like AWS and “repositories like GitHub” have worked together to keep an eye on leaked secret attack vectors and provide mitigations. But although these solutions help, Sysdig notes “it is no longer acceptable to just rely on the native alerts provided by CSPs.”
Rather, it’s time for organizations to shift focus to a complete cloud threat detection system that “includes runtime analysis and can detect advanced threats and provide enough visibility to conduct incident response should a successful attack occur,” the security and monitoring solutions provider concluded, unsurprisingly.
Keep up to date on all things cloud security. Read our security channel here.